What is a SOCKS Proxy?
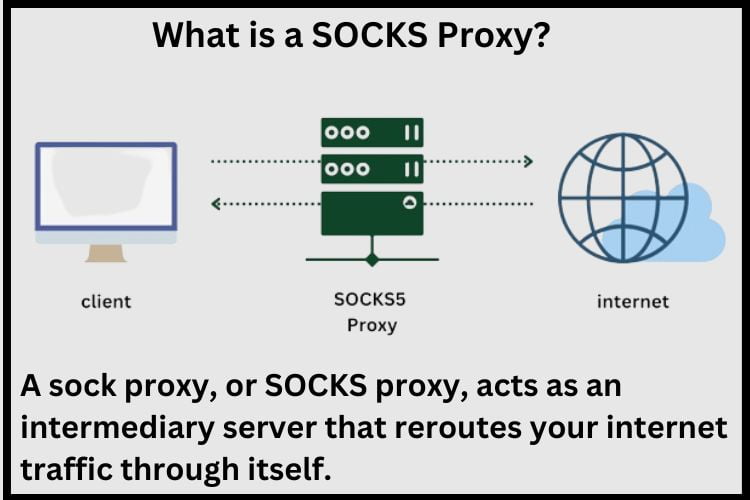
Before we search into the installation process, let’s briefly understand what a sock proxy is. A sock proxy, or SOCKS proxy, acts as an intermediary server that reroutes your internet traffic through itself. By doing so, it masks your IP address and encrypts your data, thus enhancing your online anonymity and security.
Step 1: Choose Your Proxy Provider
Before diving into the installation process, you’ll need to select a reliable SOCKS proxy provider. Look for a provider that offers high-speed connections, robust security features, and good importance for reliability and customer support.
Step 2: Obtain Your Proxy Credentials
Once you’ve chosen a provider, you’ll need to sign up for an account and obtain your proxy credentials. These typically include a hostname or IP address, a port number, and authentication details such as a username and password.
Step 3: Install a SOCKS Proxy Client
Next, you’ll need to install a SOCKS proxy client on your device. There are several options available, including open-source clients like Shadow Socks or commercial clients like Proxifier. Choose the client that best suits your needs and follow the installation instructions provided by the developer.
Step 4: Configure Your Proxy Settings
Once the client is installed, you’ll need to configure your proxy settings using the credentials provided by your proxy provider. This typically involves entering the proxy hostname or IP address, port number, and authentication details into the client’s settings menu.
Step 5: Test Your Connection
After configuring your proxy settings, it’s important to test your connection to ensure that everything is working correctly. Visit a website that detects your IP address, such as WhatIsMyIPAddress.com, to confirm that your traffic is being routed through the proxy server.
Conclusion
Installing a SOCKS proxy may seem daunting at first, but with the right guidance, it can be a straightforward process. By following the steps outlined in this guide, including selecting a reliable provider such as Proxiesforrent, you can set up a SOCKS proxy to enhance your online privacy, security, and freedom. Whether you’re a novice user or a seasoned pro, a SOCKS proxy can provide valuable benefits in today’s interconnected world.
Frequently Asked Question
Using a SOCKS proxy can provide several benefits, including enhanced privacy and anonymity, bypassing geo-restrictions, and improving network security by hiding your IP address from potential attackers.
Yes, many SOCKS proxy clients are compatible with mobile devices, including smartphones and tablets. Simply install a compatible client app from the App Store or Google Play Store and follow the same steps outlined in this guide to configure your proxy settings.
Since your internet traffic is being rerouted through an intermediary server, there may be a slight decrease in speed. However, the impact is typically minimal, especially with high-quality proxy services.
In most cases, you’ll need to configure each application or device separately to use the SOCKS proxy. However, some proxy software may offer options for global proxy settings that apply to all network traffic.
SOCKS proxies can enhance security by masking your IP address and encrypting traffic between your device and the proxy server. However, the level of security may vary depending on the proxy provider and configuration.
Unlike HTTP/HTTPS proxies that operate at the application layer, SOCKS proxies work at the transport layer, making them capable of handling a wider range of traffic types, including TCP and UDP. This versatility makes SOCKS proxies suitable for various applications, such as web browsing, torrenting, and online gaming.



