What Is a Proxy Server?
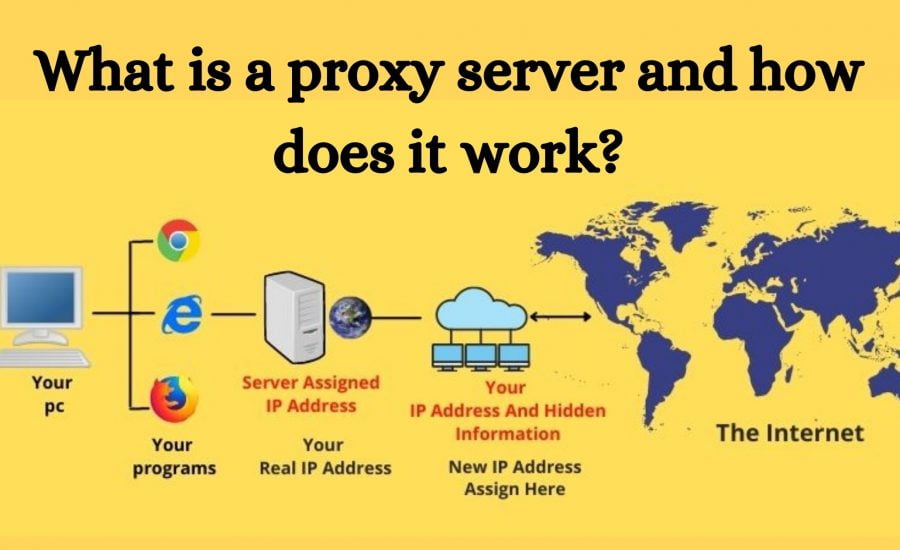
A proxy server acts as an intermediary between your device and the internet. When you send a request to access a website or online service, instead of directly connecting to the destination server, your request first goes through the proxy server. This server then forwards your request to the target server on your behalf, receives the response, and sends it back to you.
How Does a Proxy Server Work?
When you send a request to access a website, your device communicates with the proxy server first. The proxy server then forwards your request to the website on your behalf. Once the website responds, the proxy server sends the data back to your device. This process effectively protects your device’s identity and IP address from the website you’re accessing.
Why Are Proxy Servers Used?
Proxy servers serve various purposes, including:
1.Anonymity
By masking your IP address, proxy servers enable anonymous browsing, protecting your privacy online.
2.Access Control
Organizations use proxy servers to regulate internet access, restricting or granting access to specific websites or content.
3.Content Filtering
Proxy servers can filter web content, blocking access to malicious or inappropriate websites.
4.Improved Performance
Caching frequently accessed resources can speed up access to websites and reduce bandwidth usage.
5.Security
Proxy servers can act as a wall between your device and potentially harmful content, offering an additional layer of security.
6.Caching
By caching frequently accessed resources, proxy servers can improve network performance and reduce bandwidth usage, especially in environments with multiple users accessing similar content.

Types of Proxy Servers
1.Forward Proxy
This type of proxy server retrieves data from the internet on behalf of a client. It is commonly used to bypass internet restrictions in workplaces or schools.
2.Reverse Proxy
A reverse proxy retrieves resources from servers on behalf of clients. It is often used to enhance security and performance for web servers by caching content and distributing incoming requests across multiple servers.
3.Private Proxy
Private proxies provide exclusive access to a single user. This ensures enhanced security, faster speeds, and greater reliability, making them ideal for individuals or businesses with specific privacy and performance requirements.
4.Transparent Proxy
Transparent proxies intercept web traffic without requiring any configuration on the client’s end. Users may not even be aware of their presence.
5.Anonymous Proxy
These proxies conceal the user’s IP address and identity, providing a higher level of privacy.
6.High Anonymity Proxy
Similar to anonymous proxies, high anonymity proxies do not reveal any information about the user, making it extremely difficult for websites to track their activities.
7.Shared Proxy
Shared proxies, as the name suggests, are utilized by multiple users simultaneously. While they offer cost-effectiveness, they may also be prone to slower speeds and potential security risks due to multiple users accessing the same IP address.
Conclusion
In proxiesforrent, where online privacy, security, and accessibility are paramount concerns, proxy servers emerge as necessary tools for navigating the digital landscape. Whether you’re seeking to protect your identity, bypass geo-restrictions, or optimize network performance, understanding the fundamentals of proxy servers empowers you to harness their capabilities effectively.
Frequently Asked Question
Proxy servers can help bypass geo-restrictions by making it appear as though the user is accessing the internet from a different location.
In some cases, using a proxy server can just reduce internet speed due to the additional step of routing traffic through the proxy. However, this impact is often minor, especially with high-quality proxy services and fast internet connections.
Proxy servers can be configured on various devices, including computers, smartphones, tablets, and even routers, depending on the compatibility and settings supported by the device’s operating system or network configuration.
No, not all proxy servers offer encryption. Some only act as intermediaries without encrypting the data passing through them. For encryption, consider using a VPN (Virtual Private Network) instead.
Proxy servers primarily support HTTP and HTTPS protocols, although some may also work with other protocols such as FTP, SOCKS, and SMTP, depending on their configuration.
Setting up a proxy server involves configuring network settings on your device or using dedicated software provided by the proxy service provider.